Packet Tracer - 使用 CLI 配置 IOS 入侵防御系统 (IPS)
Packet Tracer - 使用 CLI 配置 IOS 入侵防御系统 (IPS)
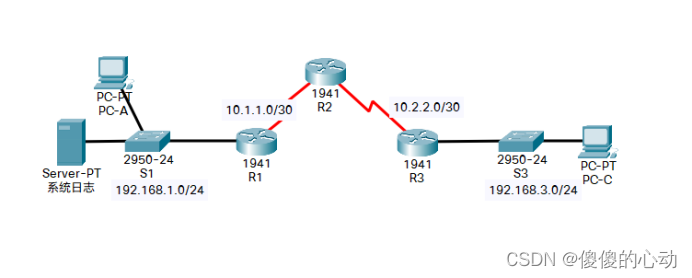
拓扑图
地址分配表
| 设备 | 接口 | IP 地址 | 子网掩码 | 默认网关 | 交换机端口 |
| R1 | G0/1 | 192.168.1.1 | 255.255.255.0 | 不适用 | S1 F0/1 |
| S0/0/0 | 10.1.1.1 | 255.255.255.252 | 不适用 | 不适用 | |
| R2 | S0/0/0 (DCE) | 10.1.1.2 | 255.255.255.252 | 不适用 | 不适用 |
| S0/0/1 (DCE) | 10.2.2.2 | 255.255.255.252 | 不适用 | 不适用 | |
| R3 | G0/1 | 192.168.3.1 | 255.255.255.0 | 不适用 | S3 F0/1 |
| S0/0/0 | 10.2.2.1 | 255.255.255.252 | 不适用 | 不适用 | |
| 系统日志 | NIC | 192.168.1.50 | 255.255.255.0 | 192.168.1.1 | S1 F0/2 |
| PC-A | NIC | 192.168.1.2 | 255.255.255.0 | 192.168.1.1 | S1 F0/3 |
| PC-C | NIC | 192.168.3.2 | 255.255.255.0 | 192.168.3.1 | S3 F0/2 |
目标
· 启用 IOS IPS。
· 配置日志记录。
· 修改 IPS 签名。
· 验证 IPS。
背景/ 场景
您的任务是在 R1 上启用 IPS 以扫描进入 192.168.1.0 网络的流量。
标记为“syslog”(系统日志)的服务器用于记录 IPS 消息。您 必须配置路由器,以确定将接收日志记录 消息的系统日志服务器。使用系统日志 (syslog) 监控网络时 ,在系统日志 (syslog) 消息中显示正确的时间和日期至关重要。设置时钟并配置时间戳 服务,以登录路由器。最后,启用 IPS 以生成警报并 以内联方式丢弃 ICMP 回应应答数据包。
已预配置服务器和 PC。已使用 以下信息对路由器进行了预配置:
o 启用 密码:ciscoenpa55
o 控制台 密码:ciscoconpa55
o SSH 用户名和密码:SSHadmin/ciscosshpa55
o OSPF 101
第 1 部分:启用 IOS IPS
注意:在 Packet Tracer 中,路由器已 导入并实施了签名文件。它们是闪存 中的默认 XML 文件。出于此原因,不需要配置加密 公钥和完成签名文件的手动导入。
步骤 1:启用 安全技术包。
a. 在 R1 上,发出 show version 命令以查看 安全技术包许可证信息。
b. 如果安全技术包尚未启用,请使用 以下命令启用技术包。
R1(config)#license boot module c1900 technology-package securityk9
c. 接受最终用户许可协议。
d. 保存运行配置并重新加载该路由器以启用安全 许可证。
R1#write
Building configuration...
[OK]
R1#reload
e. 使用 show version 命令验证是否启用了安全技术包。
R1#show version
Cisco IOS Software, C1900 Software (C1900-UNIVERSALK9-M), Version 15.1(4)M4, RELEASE SOFTWARE (fc2)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2007 by Cisco Systems, Inc.
Compiled Wed 23-Feb-11 14:19 by pt_team
ROM: System Bootstrap, Version 15.1(4)M4, RELEASE SOFTWARE (fc1)
cisco1941 uptime is 8 minutes, 51 seconds
System returned to ROM by power-on
System image file is "flash0:c1900-universalk9-mz.SPA.151-1.M4.bin"
Last reload type: Normal Reload
This product contains cryptographic features and is subject to United
States and local country laws governing import, export, transfer and
use. Delivery of Cisco cryptographic products does not imply
third-party authority to import, export, distribute or use encryption.
Importers, exporters, distributors and users are responsible for
compliance with U.S. and local country laws. By using this product you
agree to comply with applicable laws and regulations. If you are unable
to comply with U.S. and local laws, return this product immediately.
A summary of U.S. laws governing Cisco cryptographic products may be found at:
http://www.cisco.com/wwl/export/crypto/tool/stqrg.html
If you require further assistance please contact us by sending email to
export@cisco.com.
Cisco CISCO1941/K9 (revision 1.0) with 491520K/32768K bytes of memory.
Processor board ID FTX152400KS
2 Gigabit Ethernet interfaces
2 Low-speed serial(sync/async) network interface(s)
DRAM configuration is 64 bits wide with parity disabled.
255K bytes of non-volatile configuration memory.
249856K bytes of ATA System CompactFlash 0 (Read/Write)
License Info:
License UDI:
-------------------------------------------------
Device# PID SN
-------------------------------------------------
*0 CISCO1941/K9 FTX15241P4M
Technology Package License Information for Module:'c1900'
----------------------------------------------------------------
Technology Technology-package Technology-package
Current Type Next reboot
-----------------------------------------------------------------
ipbase ipbasek9 Permanent ipbasek9
security securityk9 Evaluation securityk9
data disable None None
Configuration register is 0x2102
R1#
步骤 2:验证 网络连接。
- 从 PC-C 对 PC-A 执行 ping 操作。该 ping 操作应该能够成功。
- 从 PC-A 对 PC-C 执行 ping 操作。该 ping 操作应该能够成功。
步骤 3:在闪存中创建 IOS IPS 配置目录。
在 R1 上,使用 mkdir 命令在闪存中创建一个目录。将目录命名为 ipsdir。
R1#mkdir ipsdir
Create directory filename [ipsdir]?
Created dir flash:ipsdir
R1#
步骤 4:配置 IPS 签名存储位置。
在 R1 上,将 IPS 签名存储位置配置为 你刚刚创建的目录。
R1(config)#ip ips config location flash:ipsdir
步骤 5:创建 IPS 规则。
在 R1 上,在全局配置模式下使用 ip ips name name 命令创建 IPS 规则名称。将 IPS 规则命名为 iosips。
R1(config)#ip ips name iosips
步骤 6:启用日志记录。
IOS IPS 支持使用系统日志发送事件 通知。默认情况下,启用系统日志通知。如果启用了日志记录控制台 ,会显示 IPS 系统日志消息。
- 启用系统日志(如果未启用)。
R1(config)#ip ips notify log
- 如有必要,在特权 EXEC 模式 下使用 clock set 命令重置时钟。
R1#clock set 10:20:00 10 May 2023
- 使用 show run 命令验证是否在路由器 上启用了日志记录的时间戳服务。启用时间戳服务(如果 未启用)。
R1(config)#service timestamps log datetime msec
d. 将日志消息发送到 IP 地址为 192.168.1.50 的系统日志服务器。
R1(config)#logging host 192.168.1.50
步骤 7: 配置 IOS IPS 以使用签名类别。
使用 retired true 命令停用全部签名 类别(签名 版本中的所有签名)。使用 retired false 命令取消停用 IOS_IPS Basic 类别。
R1(config)#ip ips signature-category
R1(config-ips-category)#category all
R1(config-ips-category-action)#retired true
R1(config-ips-category-action)#exit
R1(config-ips-category)#category ios_ips basic
R1(config-ips-category-action)#retired false
R1(config-ips-category-action)#exit
R1(config-ips-category)#exit
Do you want to accept these changes? [confirm]
Applying Category configuration to signatures ...
%IPS-6-ENGINE_BUILDING: atomic-ip - 288 signatures - 6 of 13 engines
%IPS-6-ENGINE_READY: atomic-ip - build time 30 ms - packets for this engine will be scanned
R1(config)#
步骤 8:向接口应用 IPS 规则。
在接口配置模式下使用 ip ips name direction 命令向接口应用 IPS 规则。将 R1 上的 G0/1 接口应用出站规则 。启用 IPS 后,部分日志消息 将被发送到控制台线路,表明 IPS 引擎已被 初始化。
注意:方向 in 表示 IPS 只检查进入该接口的流量。同样地,out 表示 IPS 只检查从该接口传出的流量。
R1(config)#interface g0/1
R1(config-if)#ip ips iosips out
R1(config-if)#
第 2 部分:修改 签名
步骤 1:更改签名的 事件操作。
取消停用回应请求签名(签名 2004, 子签名 ID 为 0),启用它,然后将签名操作更改为报警和丢弃。
R1(config)#ip ips signature-definition
R1(config-sigdef)#signature 2004 0
R1(config-sigdef-sig)#status
R1(config-sigdef-sig-status)#retired false
R1(config-sigdef-sig-status)#enabled true
R1(config-sigdef-sig-status)#exit
R1(config-sigdef-sig)#engine
R1(config-sigdef-sig-engine)#event-action produce-alert
R1(config-sigdef-sig-engine)#event-action deny-packet-inline
R1(config-sigdef-sig-engine)#exit
R1(config-sigdef-sig)#exit
R1(config-sigdef)#exit
Do you want to accept these changes? [confirm]
%IPS-6-ENGINE_BUILDS_STARTED:
%IPS-6-ENGINE_BUILDING: atomic-ip - 303 signatures - 3 of 13 engines
%IPS-6-ENGINE_READY: atomic-ip - build time 480 ms - packets for this engine will be scanned
%IPS-6-ALL_ENGINE_BUILDS_COMPLETE: elapsed time 648 ms
R1(config)#
步骤 2:使用 show 命令验证 IPS。
使用 show ip ips all 命令 查看 IPS 配置状态摘要。
向哪些接口应用 iosips 规则,沿什么方向应用该规则?
G0/1 ,出站。
步骤 3:验证 IPS 是否正常工作。
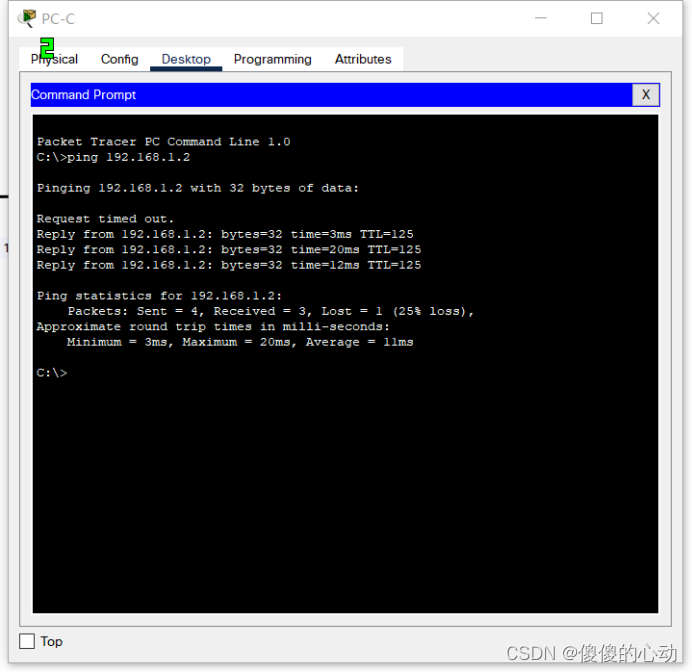
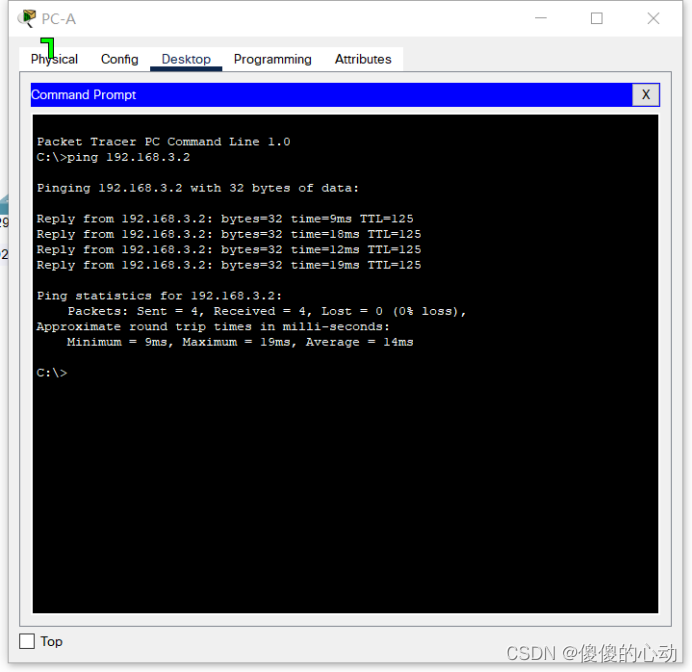
- 从 PC-C 尝试对 PC-A 执行 ping 操作。ping 操作是否成功?说明原因。
- 从 PC-A 尝试对 PC-C 执行 ping 操作。ping 操作是否成功?说明原因。
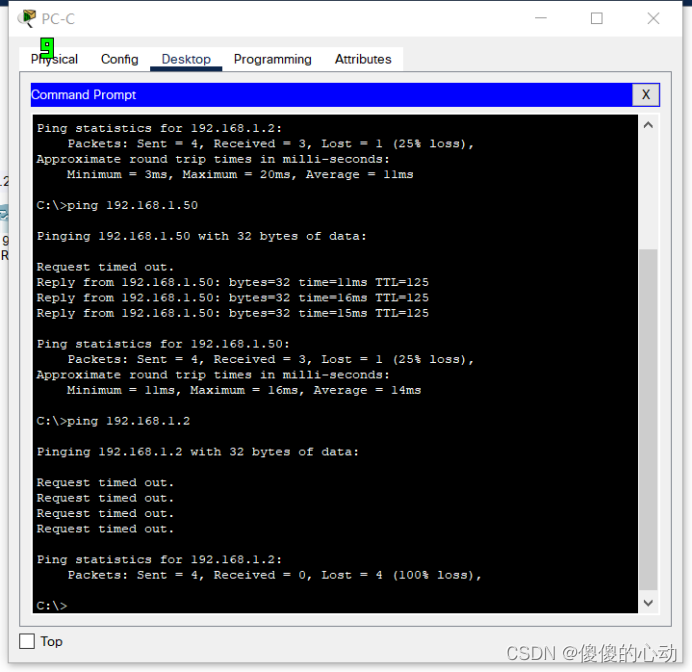
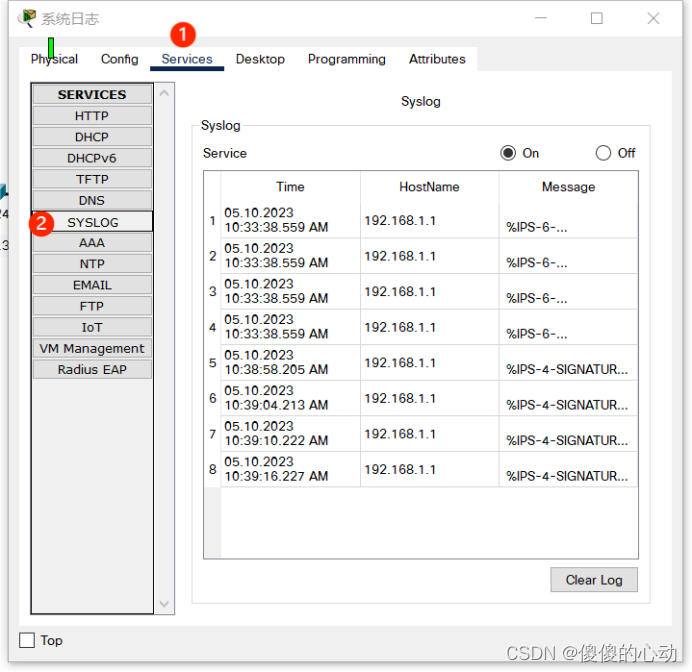
步骤 4:查看系统日志 消息。
- 点击 Syslog(系统日志)服务器。
- 选择 Services(服务)选项卡。
- 在左侧的导航菜单中,选择 SYSLOG(系统日志)以查看该日志文件。
步骤 5:检查 结果。
完成比例应为 100%。点击 Check Results(检查结果)以查看反馈并验证已 完成的所需组件。
实验具体步骤:
R1:
R1>en
Password:
R1#conf
Configuring from terminal, memory, or network [terminal]?
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#license boot module c1900 technology-package securityk9
PLEASE READ THE FOLLOWING TERMS CAREFULLY. INSTALLING THE LICENSE OR
LICENSE KEY PROVIDED FOR ANY CISCO PRODUCT FEATURE OR USING SUCH
PRODUCT FEATURE CONSTITUTES YOUR FULL ACCEPTANCE OF THE FOLLOWING
TERMS. YOU MUST NOT PROCEED FURTHER IF YOU ARE NOT WILLING TO BE BOUND
BY ALL THE TERMS SET FORTH HEREIN.
Use of this product feature requires an additional license from Cisco,
together with an additional payment. You may use this product feature
on an evaluation basis, without payment to Cisco, for 60 days. Your use
of the product, including during the 60 day evaluation period, is
subject to the Cisco end user license agreement
http://www.cisco.com/en/US/docs/general/warranty/English/EU1KEN_.html
If you use the product feature beyond the 60 day evaluation period, you
must submit the appropriate payment to Cisco for the license. After the
60 day evaluation period, your use of the product feature will be
governed solely by the Cisco end user license agreement (link above),
together with any supplements relating to such product feature. The
above applies even if the evaluation license is not automatically
terminated and you do not receive any notice of the expiration of the
evaluation period. It is your responsibility to determine when the
evaluation period is complete and you are required to make payment to
Cisco for your use of the product feature beyond the evaluation period.
Your acceptance of this agreement for the software features on one
product shall be deemed your acceptance with respect to all such
software on all Cisco products you purchase which includes the same
software. (The foregoing notwithstanding, you must purchase a license
for each software feature you use past the 60 days evaluation period,
so that if you enable a software feature on 1000 devices, you must
purchase 1000 licenses for use past the 60 day evaluation period.)
Activation of the software command line interface will be evidence of
your acceptance of this agreement.
ACCEPT? [yes/no]: yes
% use 'write' command to make license boot config take effect on next boot
R1(config)#: %IOS_LICENSE_IMAGE_APPLICATION-6-LICENSE_LEVEL: Module name = C1900 Next reboot level = securityk9 and License = securityk9
R1(config)#end
R1#
%SYS-5-CONFIG_I: Configured from console by console
R1#write
Building configuration...
[OK]
R1#reload
R1#mkdir ipsdir Create directory filename [ipsdir]? Created dir flash:ipsdir
R1#conf
Configuring from terminal, memory, or network [terminal]?
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#ip ips config location flash:ipsdir R1(config)#ip ips name iosips R1(config)#ip ips notify log R1(config)#end
R1#
%SYS-5-CONFIG_I: Configured from console by console
R1#clock set 10:20:00 10 May 2023
R1#
R1#conf
Configuring from terminal, memory, or network [terminal]?
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#service timestamps log datetime msec R1(config)#logging host 192.168.1.50 R1(config)#ip ips signature-category R1(config-ips-category)#category all R1(config-ips-category-action)#retired true R1(config-ips-category-action)#exit R1(config-ips-category)#category ios_ips basic R1(config-ips-category-action)#retired false R1(config-ips-category-action)#exit R1(config-ips-category)#exit Do you want to accept these changes? [confirm]
R1(config)#interface g0/1 R1(config-if)#ip ips iosips out R1(config-if)# R1(config-if)#exit R1(config)#ip ips signature-definition R1(config-sigdef)#signature 2004 0 R1(config-sigdef-sig)#status R1(config-sigdef-sig-status)#retired false R1(config-sigdef-sig-status)#enabled true R1(config-sigdef-sig-status)#exit R1(config-sigdef-sig)#engine R1(config-sigdef-sig-engine)#event-action produce-alert R1(config-sigdef-sig-engine)#event-action deny-packet-inline R1(config-sigdef-sig-engine)#exit R1(config-sigdef-sig)#exit R1(config-sigdef)#exit Do you want to accept these changes? [confirm] R1(config)#end R1#wr Building configuration... [OK] R1#
实验脚本:
R1:
en conf t license boot module c1900 technology-package securityk9 yes end write reload
enable mkdir ipsdir conf t ip ips config location flash:ipsdir ip ips name iosips ip ips notify log end clock set 10:20:00 10 May 2023 conf t service timestamps log datetime msec logging host 192.168.1.50 ip ips signature-category category all retired true exit category ios_ips basic retired false exit exit interface g0/1 ip ips iosips out exit ip ips signature-definition signature 2004 0 status retired false enabled true exit engine event-action produce-alert event-action deny-packet-inline exit exit exit end wr
实验链接:https://pan.baidu.com/s/1MQZjgTCbnCLoGRzQ6z_Xow?pwd=5412
提取码:5412
--来自百度网盘超级会员V2的分享